A key supplier in Apple’s global manufacturing network has suffered a data breach that could expose confidential product-related files, underscoring growing cybersecurity risks across the technology supply chain.
According to reporting by 9to5Mac, the breach affected a company that plays a significant role in Apple’s hardware ecosystem. While Apple itself was not breached, sensitive internal documents linked to future or current products may have been accessed through the supplier’s systems.
At the time of reporting, neither Apple nor the supplier had publicly detailed the full scope of the breach, leaving questions about what data was accessed and whether it has been exfiltrated or shared.
What is known so far
The incident reportedly involved unauthorized access to internal systems at the supplier, potentially exposing design documents, manufacturing files, or other confidential materials tied to Apple products. The identity of the affected supplier was disclosed in the original report, though full technical details of the attack remain limited.
There is no public confirmation that customer data was involved, nor evidence that Apple’s own internal systems were compromised. The breach appears to be isolated to the supplier’s infrastructure.
As is common in early-stage breach disclosures, investigations are ongoing, and initial assessments may evolve as forensic analysis continues.
Why supply chain breaches are especially sensitive
Technology supply chains are increasingly complex, spanning dozens of countries and hundreds of partners. While companies like Apple invest heavily in securing their own systems, suppliers often operate under varying cybersecurity standards and regulatory environments.
This asymmetry makes suppliers attractive targets. Breaching a single vendor can provide attackers with indirect access to highly valuable intellectual property without confronting the defenses of a major technology company directly.
For Apple, whose product secrecy is a core part of its strategy, any exposure of confidential files carries reputational and competitive risks — even if no immediate leaks occur.
Implications for startups and the broader tech ecosystem
The breach highlights a challenge that extends well beyond Apple. Startups building hardware, operating platforms, or handling sensitive data increasingly depend on third-party manufacturers and service providers.
For early-stage companies, enforcing rigorous cybersecurity standards across partners can be difficult due to cost and leverage constraints. Yet incidents like this demonstrate that vulnerabilities anywhere in the supply chain can have outsized consequences.
As hardware startups scale, investors are paying closer attention to operational risk — including how companies vet and monitor suppliers’ security practices.
A growing pattern in global manufacturing
Supply chain cyberattacks have surged in recent years, affecting industries ranging from semiconductors to automotive manufacturing. Attackers recognize that suppliers often hold valuable data but lack the same defensive resources as their largest customers.
In regions where manufacturing is concentrated, a single breach can ripple across multiple companies and product lines. This dynamic raises questions about whether industry-wide security frameworks or regulatory standards are sufficient.
For multinational companies, the challenge is compounded by operating across jurisdictions with different disclosure rules and enforcement regimes.
What remains unclear
Several critical details have not yet been confirmed:
- Whether the accessed files relate to current products or unreleased hardware
- Whether any data has been publicly leaked or sold
- How long attackers had access before detection
- What remediation steps the supplier and Apple are taking
Apple has historically declined to comment on supply chain incidents unless customer data is involved, making further clarification uncertain.
U.S. and global regulatory context
Although Apple is headquartered in the United States, its supply chain spans Asia, Europe, and other regions. Data breaches involving cross-border partners can trigger regulatory obligations under multiple legal frameworks, depending on the nature of the data exposed.
At present, there is no indication that regulators have intervened. However, as governments place greater emphasis on supply chain security — particularly for critical technologies — such incidents may draw increased scrutiny.
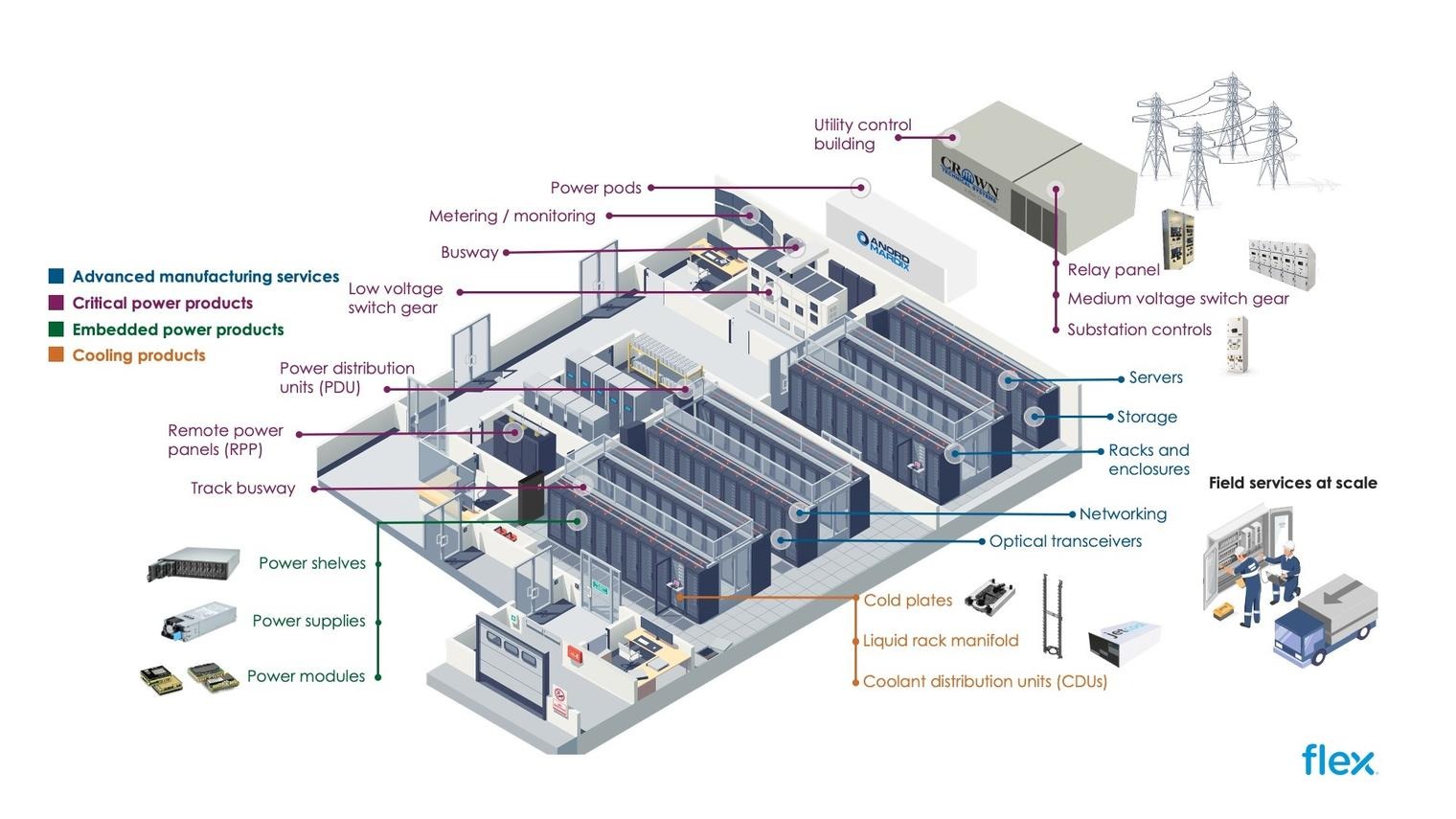
A reminder that security is only as strong as the weakest link
The supplier breach reinforces a sobering reality for the technology industry: cybersecurity is not confined to corporate headquarters or cloud infrastructure. It extends to every partner, contractor, and vendor involved in building modern devices.
For Apple, the incident is a reminder that maintaining secrecy and security requires constant vigilance beyond its own walls. For startups and established companies alike, it highlights the need to treat supply chain cybersecurity as a strategic priority rather than an operational afterthought.
As investigations continue, the industry will be watching closely — not just for what data may have been exposed, but for how companies respond when the breach is not inside their own networks, but just one step away.


![[CITYPNG.COM]White Google Play PlayStore Logo – 1500×1500](https://startupnews.fyi/wp-content/uploads/2025/08/CITYPNG.COMWhite-Google-Play-PlayStore-Logo-1500x1500-1-630x630.png)