Multiple U.S. state, county, and local government websites, along with universities and other organizations, have fallen victim to a spam campaign involving scam advertisements for hacking services.
The scammers uploaded PDF files containing these ads to official websites, including those belonging to state governments such as California, North Carolina, New Hampshire, Ohio, Washington, and Wyoming, as well as various educational institutions like UC Berkeley, Stanford, and Yale. Other affected organizations include the Red Cross in Spain, defense contractor Rockwell Collins, and an Ireland-based tourism company.
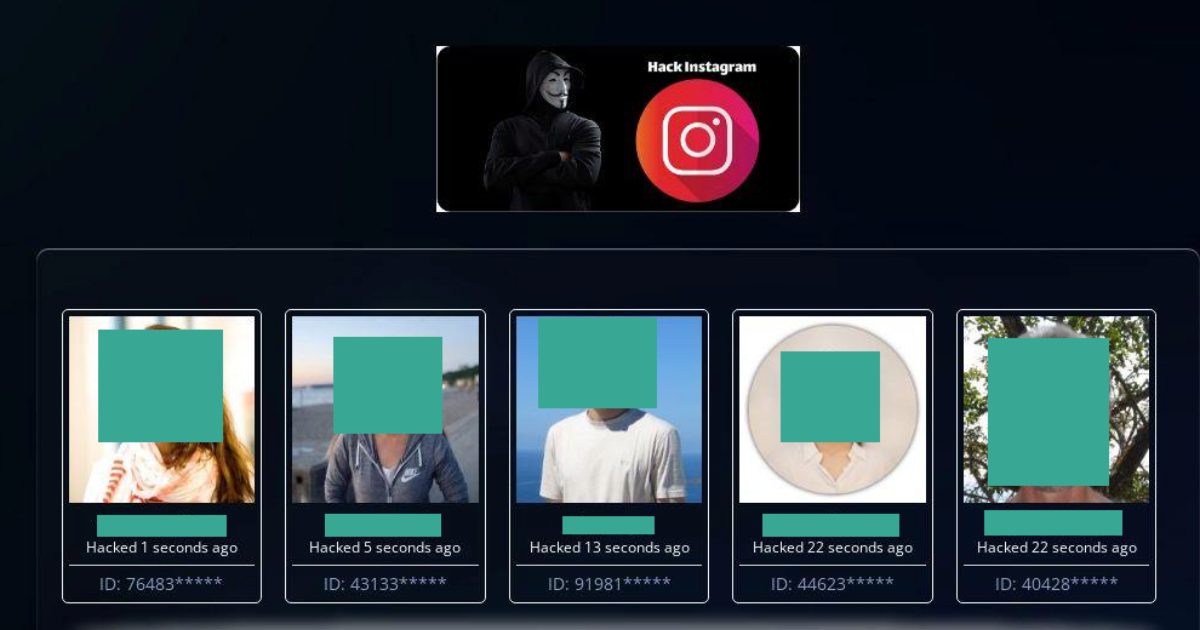
The PDFs directed users to websites claiming to offer hacking services for popular platforms like Instagram, Facebook, and Snapchat, as well as services to cheat in video games or create fake followers. While some documents appear to have been online for years, it remains unclear who is behind this large-scale spam campaign. John Scott-Railton, a senior researcher at Citizen Lab, discovered the advertisements and noted that while they seem harmless, the flaws exploited could have been used for more malicious purposes.
Upon investigation, TechCrunch found that the websites advertised in the PDFs appeared to be part of a click-fraud scheme to generate money. The cybercriminals used open-source tools to create popups and verify human visitors while secretly generating revenue. However, the advertised hacking services were likely fake, despite some sites displaying alleged victims’ profile pictures and names.
Representatives from affected organizations explained that scammers exploited flaws in online forms or content management system (CMS) software, allowing them to upload the PDFs. Kentico CMS was specifically mentioned by several victims, including the town of Johns Creek, the University of Washington, and Community Colleges of Spokane. However, not all victims attributed the issue to Kentico, and some organizations have already taken steps to remove the PDFs and address the vulnerabilities.
While the immediate impact of this spam campaign appears minimal, the ability to upload content to government websites raises concerns about the overall security of these platforms. The Cybersecurity and Infrastructure Security Agency (CISA) is aware of the compromises and is coordinating with affected entities to provide assistance. It is crucial for organizations to promptly address vulnerabilities and protect against potential threats in order to maintain the integrity and security of their websites.


![[CITYPNG.COM]White Google Play PlayStore Logo – 1500×1500](https://startupnews.fyi/wp-content/uploads/2025/08/CITYPNG.COMWhite-Google-Play-PlayStore-Logo-1500x1500-1-630x630.png)