During an analysis of various splinter samples of a noteworthy macOS stealer, security researchers at Moonlock discovered one with an alarming level of sophistication. Under the disguise of the unreleased video game GTA 6, once installed, the malware executes rather clever techniques to extract sensitive information, such as passwords from a user’s local Keychain.
In typical Security Bite fashion, here’s the breakdown: how it works and how to stay safe.
9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the most powerful and modern Apple MDM on the market. The result is a totally automated Apple Unified Platform currently trusted by over 45,000 organizations to make millions of Apple devices work-ready with no effort and at an affordable cost. Request your EXTENDED TRIAL today and understand why Mosyle is everything you need to work with Apple.

As I reported in a previous edition of Security Bite, malware specially made to target macOS continues to germinate in popularity as Mac grows in popularity. Last year, 21 new malware families were discovered in the wild, up 50% from 2022.
Despite this fact, there still exists a common misconception that threat actors do not target Apple machines. While this may have been true in the past, it is certainly not the case today. Not only is the number of malware attacks increasing, but they are also becoming more sophisticated than ever.
How it works
Moonlock, the cybersecurity division of MacPaw, found the new malware sample is a variant of password-stealing ware (PSW), a type of trojan malware designed to collect logins and passwords from infected machines and send them back to the threat actor via a remote connection or email.
The malware disguises itself as either an alleged copy of GTA 6 or a pirated version of Notion. This is a common social engineering trick that exploits trust by using familiar nomenclature to deceive users into downloading malware.
Notably, all Macs come with a version of macOS Gatekeeper installed that works in the background to prevent users from downloading unsigned applications from the Internet that could contain malware. A user, however, can override this security feature by simply right-clicking on the DMG file and hitting “Open.” Cybercriminals exploit this ease by including a graphic instructing the user on how to open the malicious file.
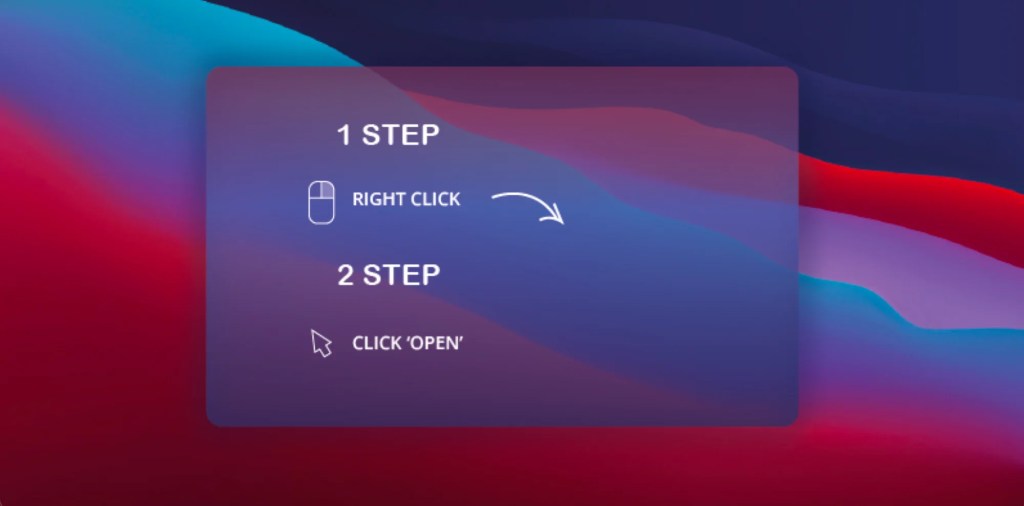
Upon execution, the DMG unleashes a Mach-O file named AppleApp.
“Subsequently, AppleApp initiates a GET request to a specific URL originating from a Russian IP address. If the connection is successful, the program will begin to download a partially obfuscated AppleScript and Bash payload. This payload is directly executed from application memory, bypassing the file system,” Moonlock stated in a blog post about the findings.
When executed, the payload uses a multi-faceted approach to achieve its malicious objectives. In this order:
- Phishing for credentials
- Targeting sensitive data
- System profiling
- Data exfiltration
Since a local Keychain database is accessible only with a user’s system password, the malware performs its second clever technique. It deploys a fake helper app installation window, further exploiting trust and tricking the user into revealing their password.
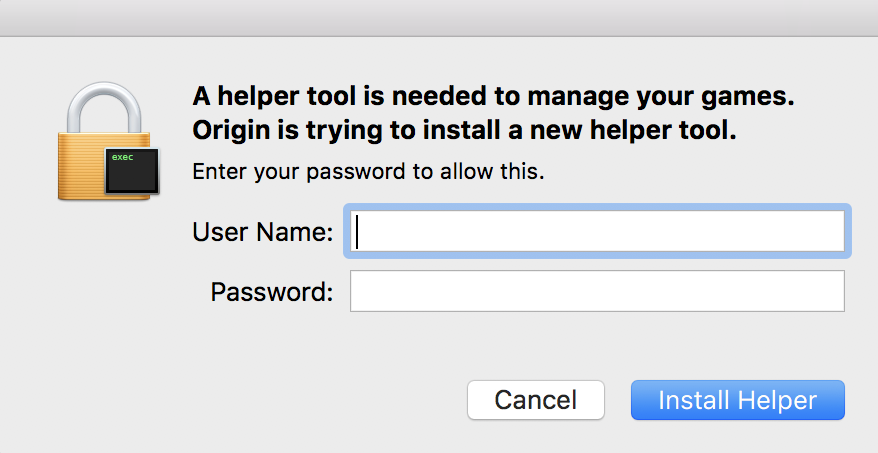
The malware now begins to target Keychain databases and many other sources of sensitive data.
“With precision, the malware hunts through system directories, looking for valuable data such as cookies, form history, and login credentials from popular web browsers including Chrome, Firefox, Brave, Edge, Opera, and OperaGX. Additionally, it seeks the recent servers list from FileZilla, macOS Keychain databases, and the wallets of cryptocurrencies.”
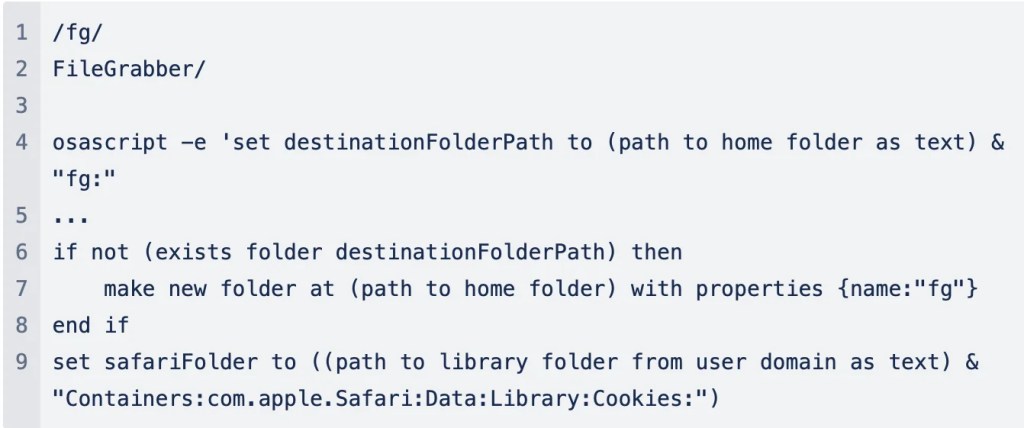
Moreover, using more sophisticated AppleScripts, the malware establishes a secret folder within users’ home directories. Here, any collected logins, passwords, and keys are stored to await extraction from the infected system to an external server controlled by the cybercriminal.
How to stay safe from macOS stealers
While only about 6% of all malware targets Mac users, threat actors are actively targeting macOS more now than ever. It’s important to stay vigilant and continue to use common Internet smarts.
While you may already know many of these tips, I think it’s important to regurgitate them again in relation to macOS stealers:
- Do your due diligence before installing anything outside the official Mac App Store
- Under no circumstance should a user follow instructions to bypass Gatekeeper
- Exercise caution with any system prompts or requests for sensitive information
- Keep your devices and applications up-to-date to protect against the latest threats and vulnerabilities
More in security
FTC: We use income earning auto affiliate links. More.



![[CITYPNG.COM]White Google Play PlayStore Logo – 1500×1500](https://startupnews.fyi/wp-content/uploads/2025/08/CITYPNG.COMWhite-Google-Play-PlayStore-Logo-1500x1500-1-630x630.png)