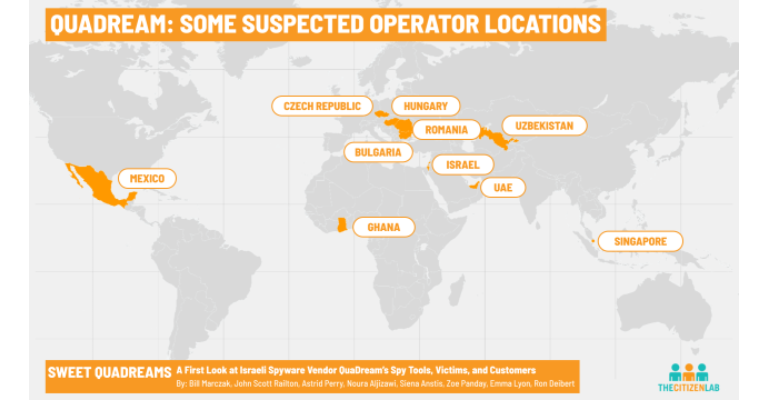
QuaDream is an Israeli cyber mercenary company that reportedly develops zero-click exploits for iPhones, which are hacking tools that don’t require the target to click on malicious links. Microsoft and digital rights group Citizen Lab analyzed samples of malware they say was created by QuaDream and found that the company’s customers operated servers from several countries around the world, including Bulgaria, Czech Republic, Hungary, Romania, Ghana, Israel, Mexico, Singapore, United Arab Emirates (UAE), and Uzbekistan, according to internet scans done by Citizen Lab.
In March 2021, Microsoft discovered that QuaDream’s customers used malicious calendar invites with dates in the past to deliver the malware to at least five victims, including an NGO worker, politicians, and journalists. The exploit used to hack those targets was developed for iOS 14, and at the time was unpatched and unknown to Apple, making it a so-called zero-day.
QuaDream’s malware has a final payload that records phone calls, records audio using the phone’s microphone surreptitiously, takes pictures, steals files, tracks the person’s granular location, and deletes forensic traces of its own existence, among other functionalities, according to Citizen Lab and Microsoft.
Citizen Lab researchers also claimed that QuaDream uses a Cyprus-based company called InReach to sell its products, allowing them to bypass Israeli export regulations. A person who has worked in the spyware industry confirmed to TechCrunch that QuaDream used InReach “to bypass the Israeli [export] regulator.”
The discovery of QuaDream’s malware shows that the spyware industry, once dominated by Hacking Team and FinFisher, is not only made up of NSO Group but several other companies, most of which are still flying under the radar.


![[CITYPNG.COM]White Google Play PlayStore Logo – 1500×1500](https://startupnews.fyi/wp-content/uploads/2025/08/CITYPNG.COMWhite-Google-Play-PlayStore-Logo-1500x1500-1-630x630.png)