At this year’s annual hacking conference, Black Hat Asia, a team of security researchers revealed how cybercriminals are sneakily using stolen credit cards and Apple Store Online’s ‘Someone else will pick it up’ option in a scheme that has stolen over $400,000 in just two years.
9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the most powerful and modern Apple MDM on the market. The result is a totally automated Apple Unified Platform currently trusted by over 45,000 organizations to make millions of Apple devices work-ready with no effort and at an affordable cost. Request your EXTENDED TRIAL today and understand why Mosyle is everything you need to work with Apple.
According to Gyuyeon Kim and Hyunho Cho with the Financial Security Institute of South Korea, in September 2022, she and her colleague uncovered a string of cyberattacks against more than 50 legitimate online stores, exposing major data breaches that had occurred. However, upon further analysis, they found threat actors were interested in more than a quick heist of user data.
The cybercriminals managed to manipulate the payment pages of these online stores to transmit credit card and personal information to their servers, in addition to the legitimate ones, to help remain undetected.
“These threat groups employed various evasion strategies to prevent detection of their phishing pages by site administrators and users, using multiple vulnerabilities and tools,” the security duo stated in their Black Hat briefing.
However, stealing credit cards was just one part of the plan.
One of the threat actor’s primary ways of cashing in was leveraging Apple Store Online’s ‘Pickup Contact’ policy, according to the study. “The ultimate objective of this operation was financial gain,” explained Kim.
The scheme starts with selling new Apple products at “discounted” prices in second-hand online stores in South Korea. From what the research describes, these appear to be the equivalent of a Craiglist or eBay. When the buyer reaches an agreement with the seller, or in this case, the threat actors, previously stolen card credit details are used to purchase the actual product from the Apple Store.
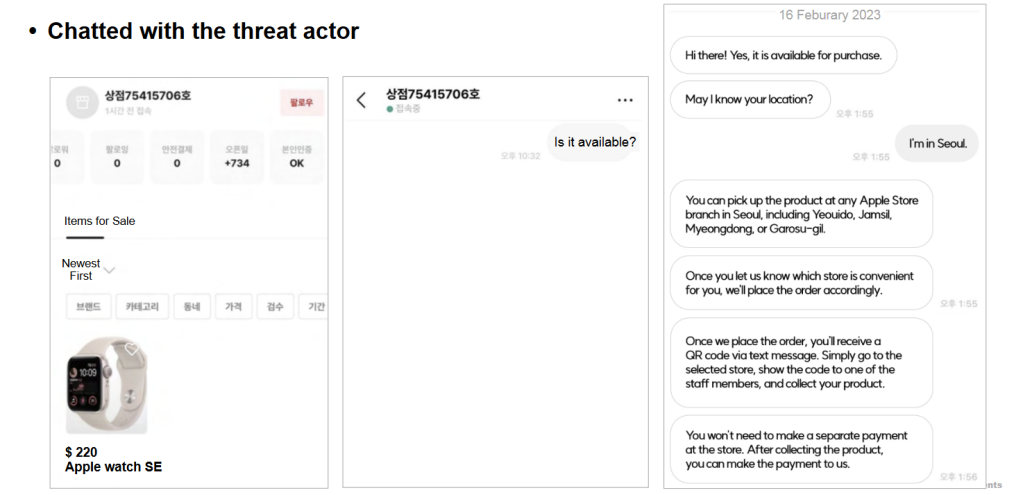
Image via Black Hat Asia/Gyuyeon Kim and Hyunho Cho
Instead of having it shipped, the cybercriminals set the item to the ‘Someone else will pick it up’ option on Apple’s website. This allows authorized individuals to pick up online orders at an Apple retail store by presenting a government photo ID and QR code/order number. The buyer from the second-hand store would be designated as the third party able to pick up the product that was unknowingly purchased with a stolen credit card.
Only after the buyer picks up the product do they pay, presumably through the second-hand store. The threat actor could miss out if the buyer doesn’t send the agreed-upon amount.
For instance, a brand-new iPhone 15 worth $800 could be listed for $700 on the second-hand market. The price would be low enough to attract interest but high enough not to appear as a scam. After finding an interested buyer, the criminals would purchase the device using a stolen credit card number obtained through their phishing operations and pocket the $700 paid by the buyer from the second-hand store.
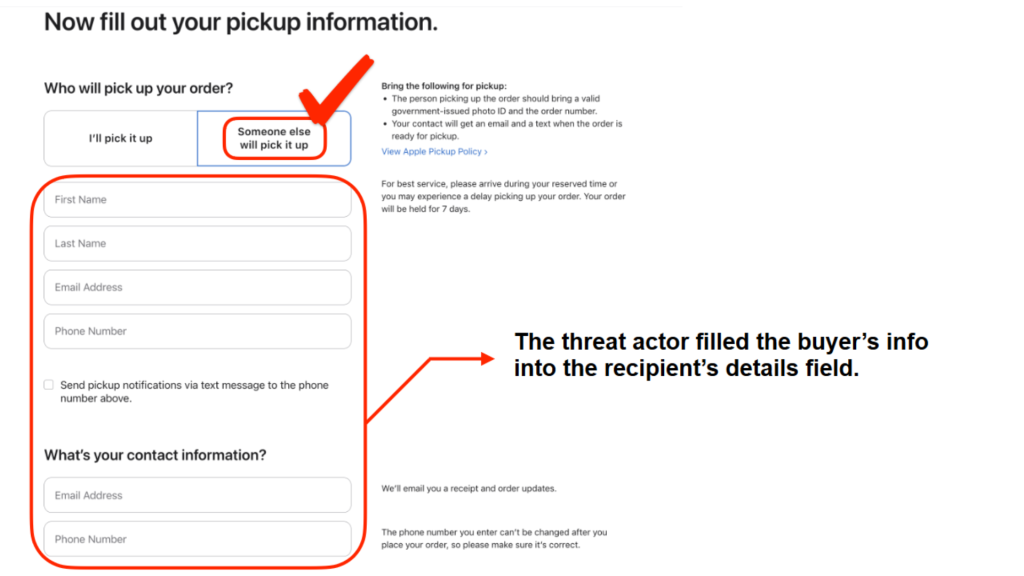
Image via Black Hat Asia/Gyuyeon Kim and Hyunho Cho
“A stolen card was used to make a $10,000 payment at an Apple store, but Apple’s refusal to cooperate due to internal regulations has hindered the investigation,” citing the researcher’s presentation at Black Hat Asia. “Despite Mr. Yoon’s efforts to report the incident to both the card company and the police immediately, Apple’s lack of cooperation has led to over a month of investigation delays. Apple’s refusal to provide any information, citing internal policy, has sparked criticism both domestically and in the United States, despite the company’s emphasis on privacy protection.”
Gyuyeon Kim and Hyunho Cho call the scheme “PoisonedApple,” which they believe has generated $400,000 over the past two years. The current scope is South Korea and Japan, but there’s no reason criminals in other countries, including the United States, could begin doing the same.
Who’s behind the scheme?
The researchers believe the culprits are based somewhere in China due to the phishing web pages being registered through a Chinese ISP. Miraculously, while combing through dark web forums, they also found mentions in simplified Chinese of the same email address in the source code.
Check out the full Black Hat briefing and presentation here.
More in this series
Follow Arin: Twitter/X, LinkedIn, Threads
FTC: We use income earning auto affiliate links. More.




![[CITYPNG.COM]White Google Play PlayStore Logo – 1500×1500](https://startupnews.fyi/wp-content/uploads/2025/08/CITYPNG.COMWhite-Google-Play-PlayStore-Logo-1500x1500-1-630x630.png)