Cloud security provider Wiz has discovered an incident that occurred in July 2020, where a misconfigured link inadvertently exposed approximately 38TB of sensitive Microsoft data. After nearly three years of this data being accessible, the security firm uncovered this issue while scanning the internet for exposed storage accounts.
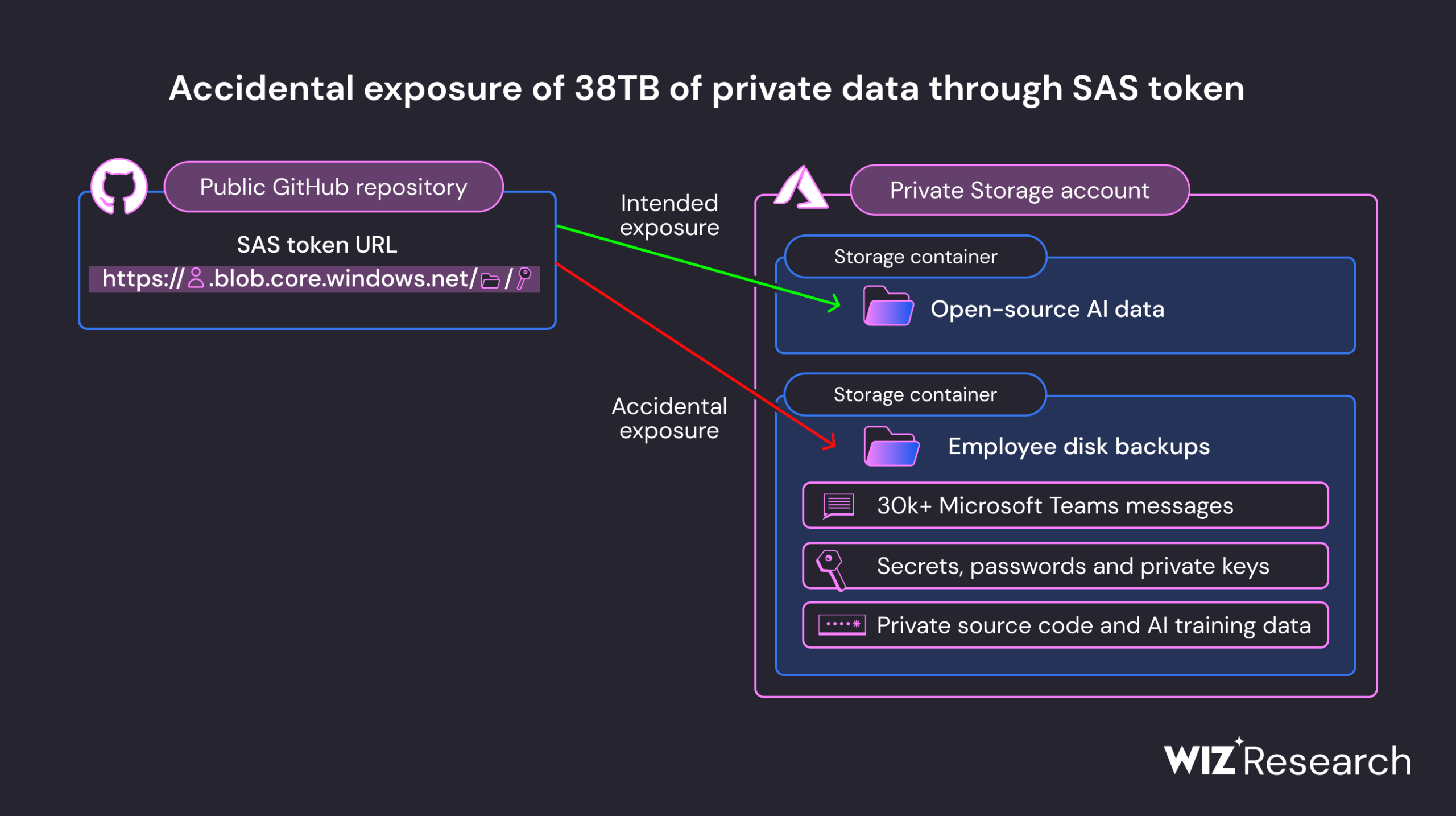
The breach originated from a software repository hosted on Microsoft-owned GitHub, which provides open-source code and AI models. It was determined that a Microsoft employee had unintentionally shared the URL to a misconfigured Azure Blob storage bucket, which contained this vast amount of leaked information.
Wiz’s report highlighted a concern related to the security of Shared Access Signature (SAS) tokens, emphasizing the need to limit their usage due to their inherent security risks. The report noted that these tokens are challenging to track, as Microsoft lacks a centralized method within the Azure portal for their management.
The exposed data included backups of personal information belonging to Microsoft employees, including passwords for various Microsoft services, secret keys, and an archive containing over 30,000 internal messages from 359 Microsoft employees, exchanged on the Microsoft Teams platform.
In response to the incident, the Microsoft Security Response Center (MSRC) issued an advisory on Monday, reassuring that no customer data had been exposed, and no other internal services were compromised as a result of this breach.
The exposure of this data was attributed to the use of an excessively permissive Shared Access Signature (SAS) token, which granted full control over the shared files. Wiz researchers described this Azure feature as posing challenges in terms of monitoring and revoking access, highlighting the need for enhanced security measures in this regard.
The post Microsoft Under Scrutiny After 38TB Data Leaked Via Azure Storage appeared first on Analytics India Magazine.


![[CITYPNG.COM]White Google Play PlayStore Logo – 1500×1500](https://startupnews.fyi/wp-content/uploads/2025/08/CITYPNG.COMWhite-Google-Play-PlayStore-Logo-1500x1500-1-630x630.png)