Ever wonder what malware can your Mac detect and remove without any third-party software? Recently, security researchers have correlated some bizarre macOS YARA rules used by the built-in XProtect suite with their public names. Here’s what malware it looks for…
9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the most powerful and modern Apple MDM on the market. The result is a totally automated Apple Unified Platform currently trusted by over 45,000 organizations to make millions of Apple devices work-ready with no effort and at an affordable cost. Request your EXTENDED TRIAL today and understand why Mosyle is everything you need to work with Apple.

What is XProtect?
XProtect was introduced in 2009 as part of macOS X 10.6 Snow Leopard. Initially, it was released to detect and alert users if malware was discovered in an installing file. However, over time, it has become a suite of tools as Apple continues to address the rising problem of malware on its platform.
The XProtect suite utilizes YARA signature-based detection to identify and eliminate malware. YARA is a popular open-source tool created by malware researchers, which works by identifying malware based on code similarities found in different malware families. Apple frequently adds to this pool with security updates.
As of macOS 14 Sonoma, XProtect consists of three main components:
- XProtect detects malware using YARA rules whenever an app first launches, changes, or updates its signatures.
- XProtectRemediator (XPR) can detect and remove malware by regularly performing YARA scans during periods of low activity, which have minimal impact on the CPU.
- XProtectBehaviorService (XBS) was added with the latest version of macOS and monitors system behavior in relation to critical resources.
XProtectRemediator (XPR)currently consists of 23 scanning modules that execute almost simultaneously. Unfortunately, most have generic or internal naming schemes that don’t make much sense from the outside looking in.
“The remediator part of XProtect has a series of executables…each target a particular malware family,” according to Alden, a malware researcher who recently made significant advancements by reverse engineering and identifying four scanning modules, aka remediators.
“Some rules have meaningful names like XProtect_MACOS_PIRRIT_GEN, which is a sig for the Pirrit adware, while others are generic (XProtect_MACOS_2fc5997) or internal to Apple (XProtect_snowdrift).” Alden goes into more detail on their Github.
While this is done for good reason, it can be challenging for those curious to know precisely what malware XPR is looking for.
How do I find XProtect?
XProtect is enabled by default in every version of macOS. It also runs at the system level, completely in the background, so no intervention is needed. But here’s where it’s located:
- In Macintosh HD,go to Library > Apple > System > Library > CoreServices
- From here, you can find remediators by right-clicking on XProtect
- Then click Show Package Contents
- Expand Contents > Resources
- Open MacOS
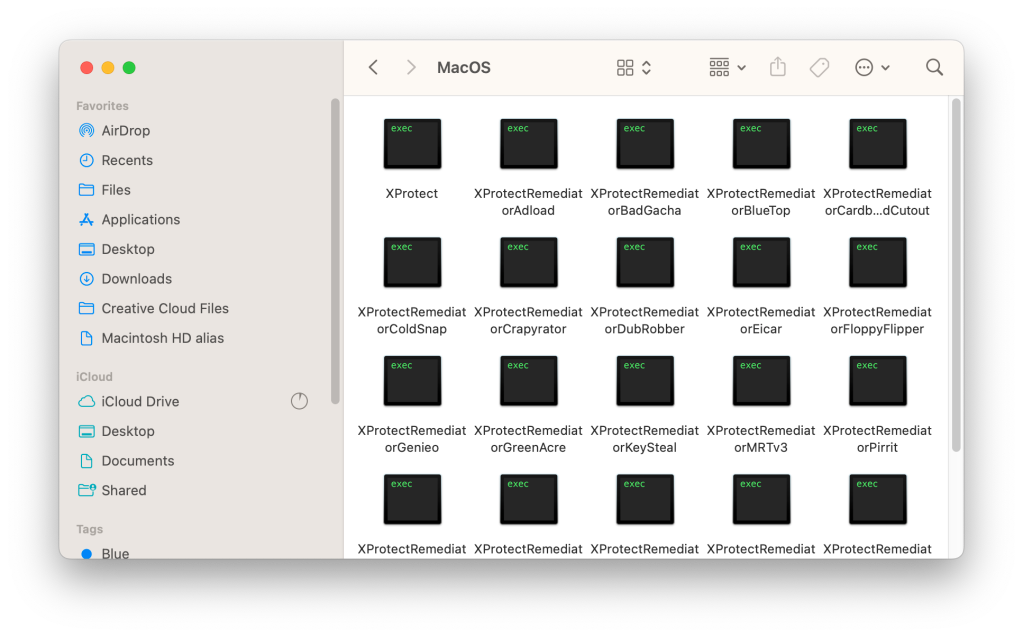
Using Alden’s new and existing findings, The Eclectic Light Company shared a list of the 14 out of 23 scanning modules in the current version of XPR and how they correlate with their public malware names. Here are a few:
lockquote class=”wp-block-quote”>
- Adload is an old adware and bundleware loader dating back to 2016 that has a track record of rapid change, enabling it to evade static detection. It normally achieves persistence through a bogus service installed in ~/Library/LaunchAgents/, and Phil Stokes gives fuller details here.
- BadGacha remains unidentified, but frequently reports false positives for helper apps in non-malicious apps.
- BlueTop is a bogus WindowServer app that was part of a Trojan-Proxy campaign investigated by Kaspersky in late 2023.
- ColdSnap is known better as SimpleTea, a cross-platform component that was part of the 3CX supply-chain attack.
- Crapyrator has been identified as BkDr.Activator, found in many torrents of cracked apps such as MarsEdit, DaisyDisk, and SpamSieve. It uses sophisticated methods, characteristically installing Activator.app in the main Applications folder, prompts for a password and uses that to disable Gatekeeper checks, then kills Notification Centre to cover its tracks. Further details are given here.
- DubRobber is known more generally as XCSSET, a versatile and troubling Trojan dropper that changes frequently to escape detection.
- Eicar isn’t malware at all, but a standard non-malicious test of detection methods.
lockquote>
I highly recommend looking at The Eclectic Light Company’s complete list. It’s eye-opening to see some of the security processes that Apple has incorporated. That said, users shouldn’t rely entirely on Apple’s XProtect suite, as it’s made to detect known threats. More advanced or sophisticated attacks could easily circumvent detection. Continue to use third-party antivirus software.
About Security Bite: Security Bite is a weekly security-focused column on 9to5Mac. Every week, Arin Waichulis delivers insights on data privacy, uncovers vulnerabilities, and sheds light on emerging threats within Apple’s vast ecosystem of over 2 billion active device s. Stay secure, stay safe.
FTC: We use income earning auto affiliate links. More.




![[CITYPNG.COM]White Google Play PlayStore Logo – 1500×1500](https://startupnews.fyi/wp-content/uploads/2025/08/CITYPNG.COMWhite-Google-Play-PlayStore-Logo-1500x1500-1-630x630.png)